Explore the Vital Duty of IT Services in Getting Your Company's Success
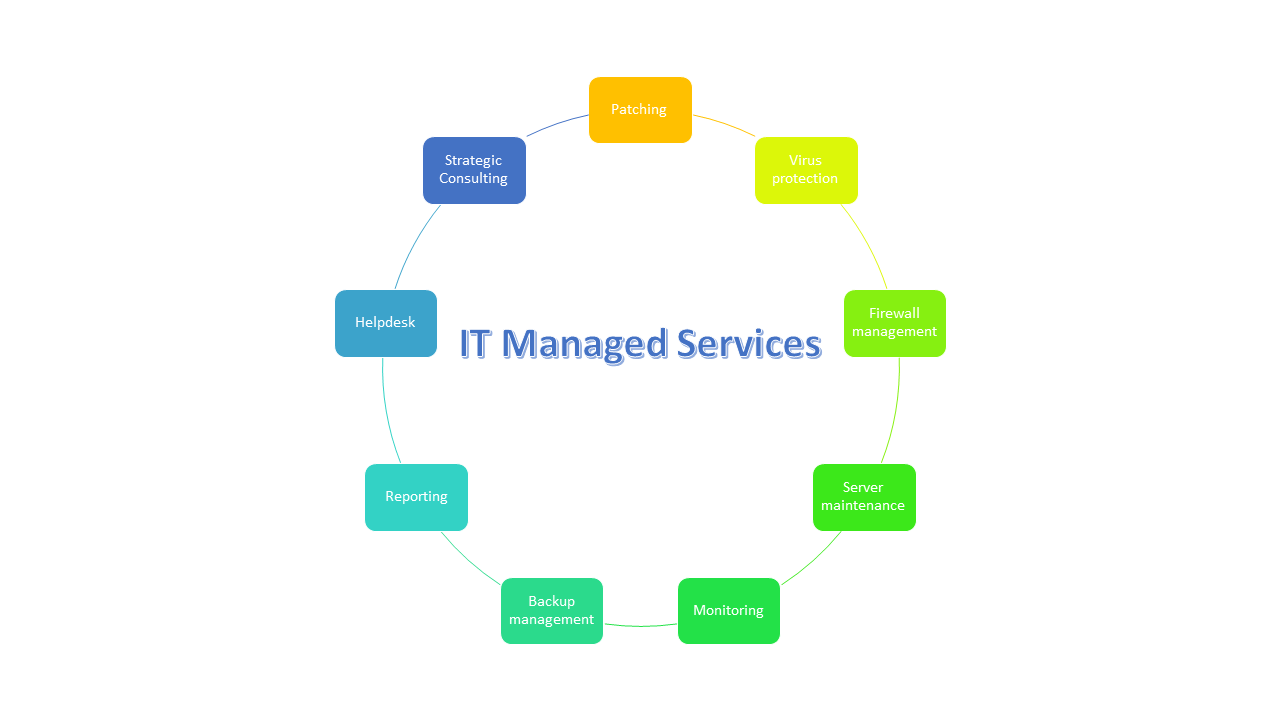
In the complex landscape of modern-day service operations, the reliance on Information Technology (IT) solutions has ended up being important for guaranteeing the safety and security and success of enterprises. Cybersecurity actions stand as the very first line of defense versus a range of electronic threats that can compromise delicate firm information and disrupt procedures. However, the duty of IT services surpasses mere protection; it reaches enhancing functional efficiency, safeguarding essential data, and making it possible for the fostering of cutting-edge technologies like cloud remedies. The tactical combination of IT solutions is not simply a matter of threat administration yet a vital chauffeur of lasting company development and strength in an ever-evolving digital age.
Significance of Cybersecurity Procedures
Making certain durable cybersecurity actions is crucial for protecting delicate information and preserving the depend on of stakeholders in today's interconnected electronic landscape. With the boosting frequency and elegance of cyber risks, services need to prioritize cybersecurity to alleviate threats effectively. Implementing solid protection methods aids prevent unauthorized accessibility, information violations, and monetary losses.
Cybersecurity actions incorporate a variety of techniques, including security, multi-factor authentication, normal safety audits, and employee training. File encryption transforms data into a safe and secure code, making it unreadable to unauthorized customers.
Enhancing Operational Performance
Offered the essential importance of cybersecurity measures in guarding delicate data, organizations can better strengthen their functional effectiveness by leveraging cutting-edge IT solutions. In addition, the assimilation of man-made intelligence and machine understanding modern technologies can optimize business procedures with data evaluation, predictive maintenance, and individualized client experiences.
Furthermore, IT solutions play a crucial role in boosting communication channels within a firm. Platforms such as VoIP systems and instant messaging applications boost real-time interactions, bring about quicker decision-making and analytical. Furthermore, by making use of task monitoring tools and collaboration software program, groups can collaborate successfully, track progression, and satisfy task deadlines efficiently. Basically, buying IT services not only enhances operational performance but likewise placements businesses for continual growth and competitiveness in today's electronic landscape.
Protecting Delicate Data
In the middle of the evolving landscape of cybersecurity risks, securing delicate information has ended up being extremely important for businesses seeking to keep trust with their stakeholders. In today's electronic globe, where data breaches and cyber-attacks are on the rise, protecting delicate information such as customer details, financial records, and intellectual property is vital for maintaining a competitive edge and upholding a positive reputation.
To safeguard delicate data effectively, services should apply durable safety procedures throughout their IT facilities. This includes security modern technologies to safeguard data both at rest and en route, multi-factor verification to avoid unauthorized gain access to, regular security audits and analyses to determine vulnerabilities, and worker training programs to advertise a culture of cybersecurity recognition.
In addition, deploying advanced endpoint protection services, firewalls, and breach discovery systems can help spot and mitigate prospective dangers before they rise into full-on safety events. By focusing on the security of delicate data, businesses can not just follow regulative requirements yet likewise construct count on with consumers, partners, and other stakeholders, ultimately adding to long-term success and sustainability.
Leveraging Cloud Modern Technology Solutions
The combination of cloud modern technology remedies has come to be important in boosting the operational performance and scalability of modern businesses. By leveraging cloud modern technology, companies can access a vast range of solutions and sources on a pay-as-you-go basis, removing the requirement for significant upfront financial investments in equipment and infrastructure. This scalability enables companies to change their IT sources based upon changing demands, making sure ideal efficiency and cost-efficiency.
Furthermore, cloud modern technology supplies enhanced flexibility, making it possible for staff members to access information and applications from anywhere with an internet connection. This availability cultivates collaboration among groups, boosts efficiency, and supports remote work arrangements (IT Support Services Charlotte). Additionally, cloud services supply durable data back-up and recuperation devices, ensuring company continuity when faced with unforeseen events such as natural catastrophes or cyberattacks
In addition, cloud modern technology supplies advanced safety attributes, consisting of security, accessibility controls, and danger discovery mechanisms, protecting sensitive company data from unapproved accessibility or violations. By entrusting their IT framework to trustworthy cloud company, companies can concentrate on their core operations while taking advantage of the most up to date technological advancements and sector ideal methods.
Ensuring Service Continuity

Key components of guaranteeing company continuity include conducting risk assessments, developing comprehensive connection strategies, applying back-up and recuperation options, and regularly testing and upgrading these procedures. Inevitably, focusing on service continuity not only safeguards procedures yet additionally boosts general organizational resilience and competition in the market.
Verdict
To conclude, IT services play a vital function in securing business success by implementing cybersecurity actions, boosting operational efficiency, safeguarding delicate data, leveraging cloud modern technology options, and guaranteeing company continuity. By spending in IT services, businesses can shield themselves from cyber dangers, streamline their procedures, and preserve the honesty of their information. It is important for go to the website firms to prioritize IT services to remain competitive and guard their long-lasting success.
Offered the important significance of cybersecurity actions in protecting delicate information, services can better boost their functional effectiveness by leveraging cutting-edge IT services. Furthermore, cloud services give robust information back-up and recovery devices, ensuring company connection in the face of unforeseen occasions such as all-natural disasters or cyberattacks.